Engineers at the Southwest Research Institute have discovered a vulnerability in DC fast-charging stations that could allow hackers to access your electric vehicle while you’re getting your coffee.
Power Line Communication (PLC) is a method of transmitting data through existing power cables, such as the electrical plugs in your home. It works by sending harmonic signals down the power lines and allowing a receiver at the other end to interpret and extrapolate the data in those harmonics. In this way, transmissions such as voice, video, and even everyday internet traffic can be sent and received directly over electrical wiring. This type of technology has been around since 1922.
Fast forward to today, there are approximately 40 million electric vehicles on the roads around the world. It is estimated that approximately 86% of EV owners charge their vehicles at home, and approximately 59% use public chargers weekly. There are approximately 10,000 Level 3 DC Fast Charging (DCFC) locations in the United States. This means that there are 10,000 potential hacking sites and millions of potential vulnerabilities in the United States alone.
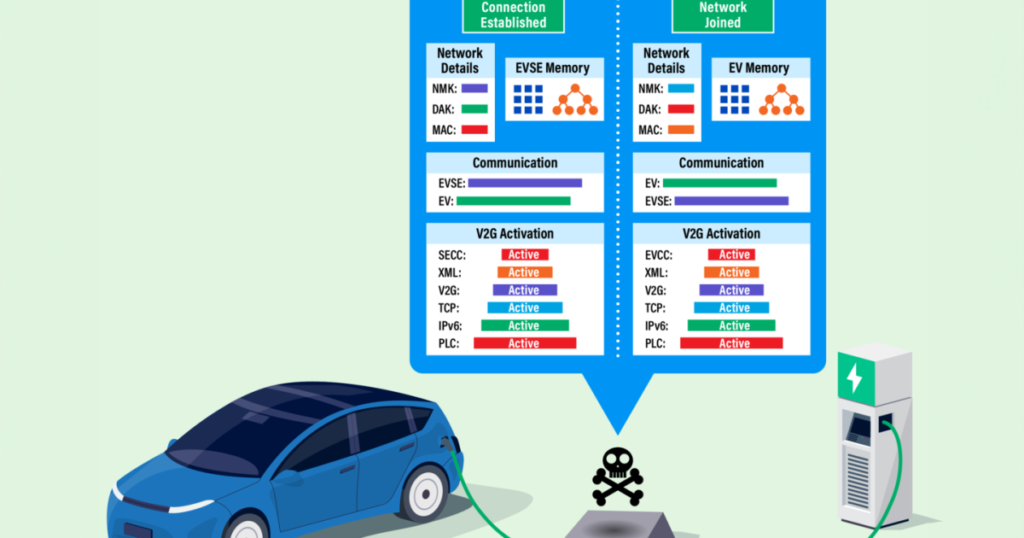
Level 3 DC chargers are the fastest way to charge your Tesla while you’re driving, and they use the IPv6-based protocol PLC to communicate with the vehicle, monitor for faults, and collect a full range of data, including charging status, state of charge, and the vehicle identification number (VIN).
SwRI exploited vulnerabilities at the PLC layer, allowing them to use a man-in-the-middle (AitM) attack that could emulate both the EV and the charging equipment, gaining access to network keys and digital addresses of both the charger and the vehicle.
“Through penetration testing, we found insufficient security at the PLC layer and insufficient encryption between the vehicle and the charger,” said Katherine Kozan, principal engineer in SwRI’s High Integrity Systems division.
Woof.
In 2020, SwRI reverse engineered and hacked the J1772 charger system, the most common charger in the US, and successfully disrupted the charging process to simulate malicious attacks. They were able to send signals to the car to mimic overcharging, throttle the charging speed, or block charging altogether.
Level 3 hacking takes everything to another level, giving would-be hackers the ability to inject code into a vehicle’s firmware (the underlying code that tells the vehicle how to operate) to alter functionality or disable it entirely. It could also give malicious hackers remote access and control via the vehicle’s cell-based internet connection.
Some readers may remember the Jeep hack from 2015, in which two hackers from Missouri took control of a Wired reporter’s unmodified Jeep Cherokee while he was driving on the highway. The hackers shut off the engine and manipulated the steering to coast the reporter off the highway and disable the brakes, all while the car’s location was monitored by GPS.
How do they achieve that kind of control? Remotely, and exclusively through the infotainment system.
“Once network access is granted via an insecure direct access key, non-volatile memory areas of a PLC-enabled device can be easily retrieved and reprogrammed, enabling destructive attacks such as firmware corruption,” said FJ Olugbodi, contributing engineer on the SwRI project.
If a malicious actor tampers with an EV firmware, it could have serious consequences for the driver and anyone else in the rogue vehicle’s path. With modern vehicles relying so heavily on software, CPUs, and internet connectivity, the possibilities are nearly endless. Essentially, the vehicle is a data center on wheels.
For example, the main brain of the new Tesla Model S is the same AMD Ryzen CPU and AMD Radeon GPU that’s in your home or work desktop computer, plus about 63 other CPUs.
Even adding encryption to an EV’s embedded systems can pose potential dangers. Failure to decrypt or authenticate data can cause the EV system to fail. Imagine trying to brake but the vehicle won’t brake because it didn’t get an authenticated signal from the pedal via the ABS module.
But all is not lost. SwRI has developed a new “zero trust” architecture that can get around layers of encryption. Zero trust works on the premise that if a bad actor tries to get through your firewall, which is likely, they can’t be stopped. But zero trust requires that each asset – laptop, server, electric car – prove its identity at the root level and prove that it belongs on the network before it can execute commands. And the network is the car itself.
Not only do all parts of the architecture need to be authenticated on every boot, but zero-trust systems also monitor the system for accuracy, identifying anomalies or unauthorized communication packets in real time if a malicious actor gains access to the vehicle’s systems.
Zero trust architectures are not being adopted in cars today, but as more and more vulnerabilities are discovered and exploited, we may see a zero trust architecture being adopted in the future.
Source: Southwest Research Institute